Now, SQLi to SHELL is one of the VM machine challenge to get shell of the server using SQLi.
PENETRATION METHODOLOGY:
- NMAP
- SQLMAP
- METASPLOIT
EXPLOITATION
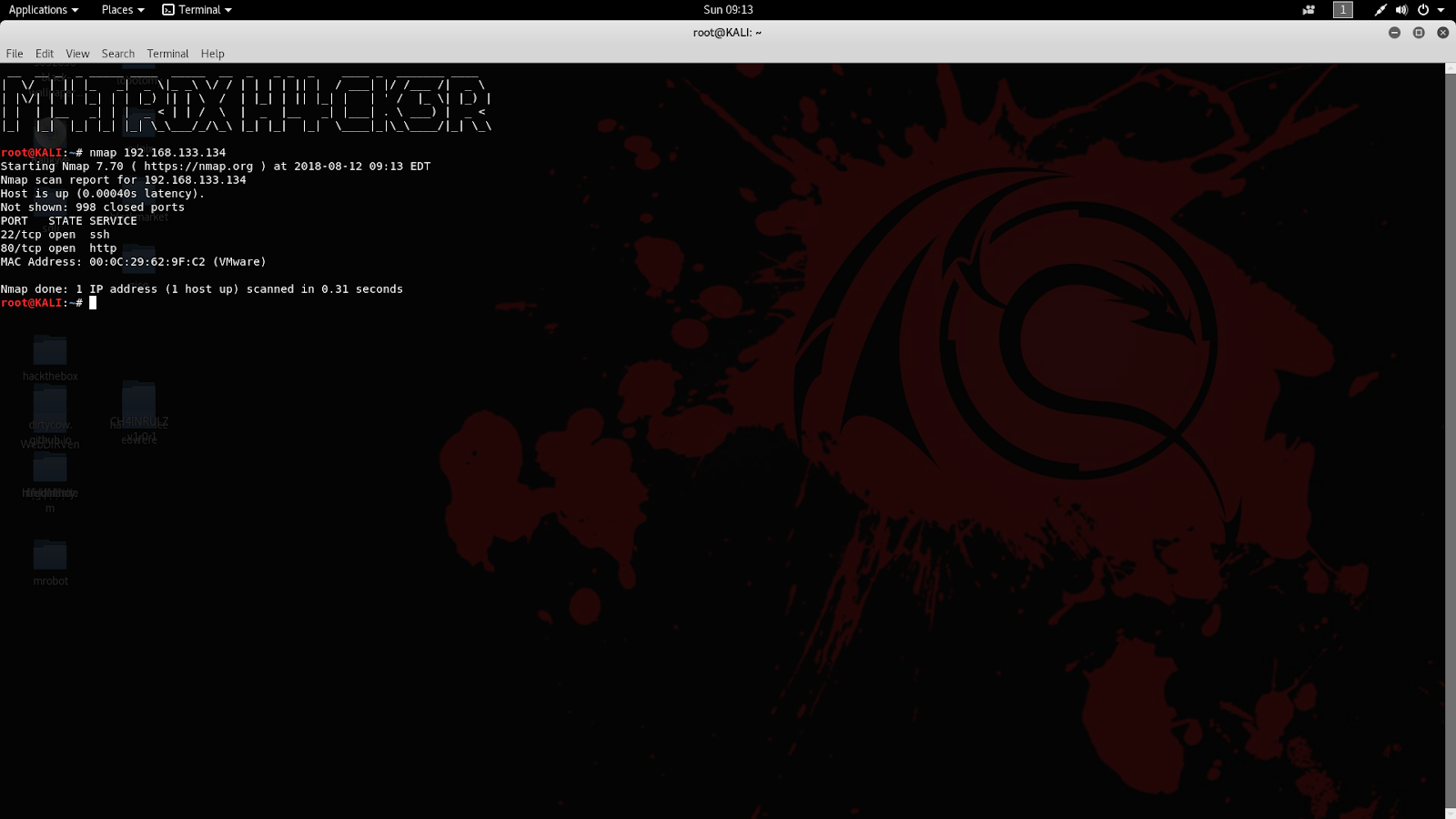
First of all, we need to enumerate the services and ports running on the server for the information gathering purpose of the target.
As the result shows that the target is running ssh and http services.
Now check the HTTP for further information gathering.
On visiting HTTP, it running a photoblog.
On further enumeration, we get that the server is vulnerable to SQLi vulnerability. As we are able to run sqlmap on the server and try to find out the user details.
On running sqlmap, we get the admin user and password.
Trying to login with this credentials and we are successful to enter in the admin panel.
Now try to upload our malicious php script and get a reverse tcp shell. We create the malicious payload using msfvenom with file extension as 'php3' because the server does not allow us to upload file on the server with extension 'php'.
Now on visiting the file we get the meterpreter reverse shell.
Now, we are in the shell of the server.
Now, this is completed.
Challenge completed by - M4TRIX_H4CK3R









Comments
Post a Comment